Ports in Linux refer to communication endpoints that allow data to flow in and out of a system. Each port is associated with a specific service or application. Furthermore, ports can be open, closed, or filtered. For instance, an open port accepts incoming packets, while a closed port rejects them. In addition, firewalls play a crucial role in managing port accessibility as well.
- Port 22 serves as the standard port for SSH (Secure Shell), allowing secure remote access to a system.
- Port 80 facilitates HTTP (Hypertext Transfer Protocol), serving web pages.
- Port 443 handles HTTPS (Hypertext Transfer Protocol Secure) traffic, ensuring encrypted communication.
Port scanning probes a system to identify open, closed, or filtered ports. You can perform port scanning using tools such as nmap or netcat. The benefits of scanning ports include:
- Regularly scanning for open ports helps identify potential vulnerabilities. Unnecessary open ports can be exploited by attackers.
- Port scanning reveals which services are running on a host. This information aids network engineers in diagnosing issues.
- By closing unnecessary ports, you reduce the attack surface, enhancing overall system security.
How to Perform a Port Scan in Your Linux System
To scan ports in your Linux system, you will need nmap tool to perform the activity on your local host or remote server.
- Install the nmap package using your package manager within your Linux server.
Downloading and Installing nmap Tool - Use the command sudo nmap -n -PN -sT -sU -p- localhost to scan ports on your local system. Breakdown of components are listed below.
- sudo: This prefix grants elevated privileges, allowing the command to run with administrative rights.
- nmap: Refers to the Nmap utility, a powerful network scanning tool used for security audits and penetration testing.
- -n: Skips DNS resolution, preventing Nmap from performing hostname lookups.
- -PN: Skips the discovery phase, assuming that the target host is online without further checks.
- -sT: Initiates a TCP connect scan, which attempts to establish a full TCP connection with each port.
- -sU: Performs a UDP scan, probing UDP ports to identify open ones.
- -p-: Scans all ports, both TCP and UDP, without specifying a port range.
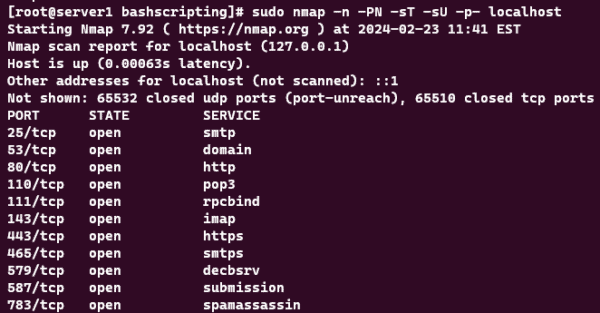
Now that you have the information related to open ports in the server, you will be able to configure the firewall that is in the system accordingly to better control the flow of traffic to your server. Making changes and optimizing the firewall would also increase your server security and provide a safer environment for your production setup.
Thank you for reading and I hope that you enjoyed this MySQL Overview in Linux guide. For more guides, please check out our Knowledge Base which is updated weekly!