Enabling root ssh login is a risky practice that can compromise the security of your system. Root SSH login allows anyone with the root password to access your system remotely and execute commands with full privileges. This can expose your system to brute force attacks, malware infections, data theft, and other threats. To prevent these risks, you should disable root SSH login and use a regular user account with sudo privileges instead.
Before proceeding, ensure that you have IPMI access or other credentials (With sudo privileges) to login to the server or you could be locking yourself out.
Disabling Direct Root Logins
To disable direct root login via SSH follow these steps:
- Within your server, use your editor of choice to open and edit the file /etc/ssh/sshd_config using the command nano, as shown below:
nano /etc/ssh/sshd_config

- Next, the document will open and you will be required to find the line PermitRootLogin yes and change it to PermitRootLogin no. Note that if there is a # character before it, then the line does not take effect as it is commented out. To activate the line, remove the # character.
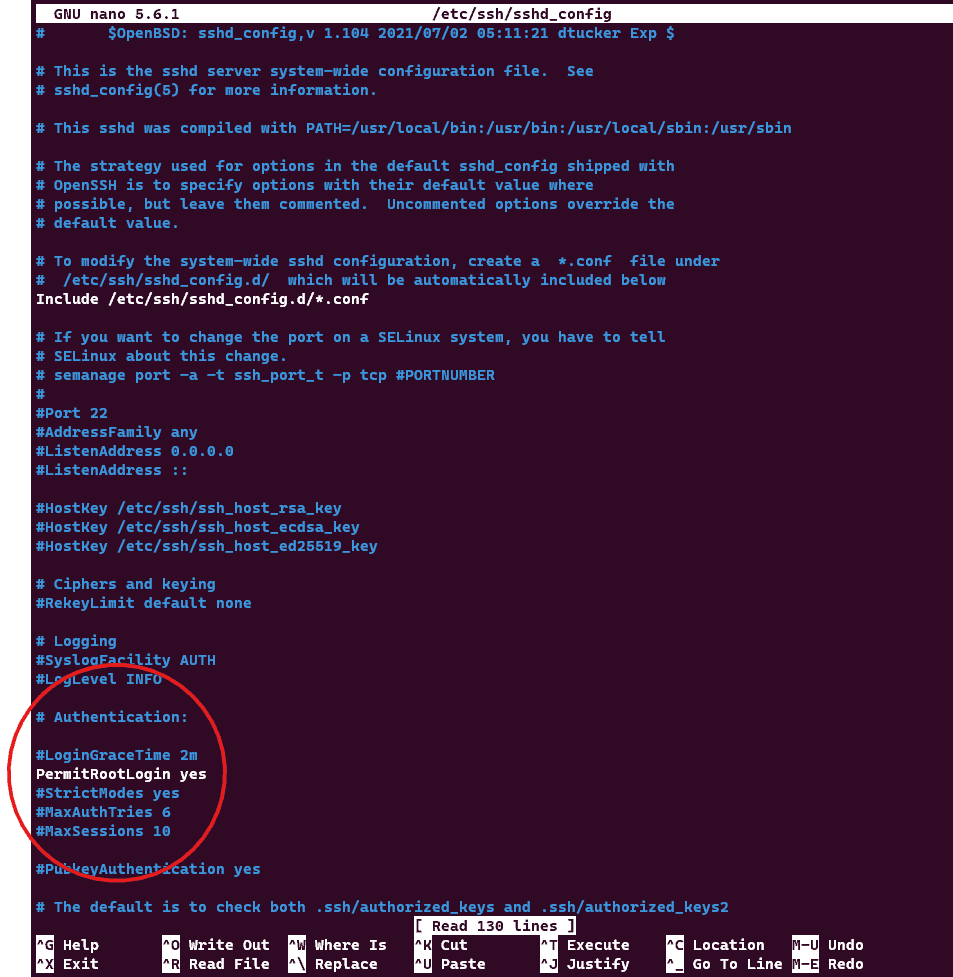
- Once the change is complete, save the document, and exit.
- Now, for the changes to take effect, we need to restart the SSH service using the command systemctl restart sshd or service sshd restart, depending on your Linux distribution.
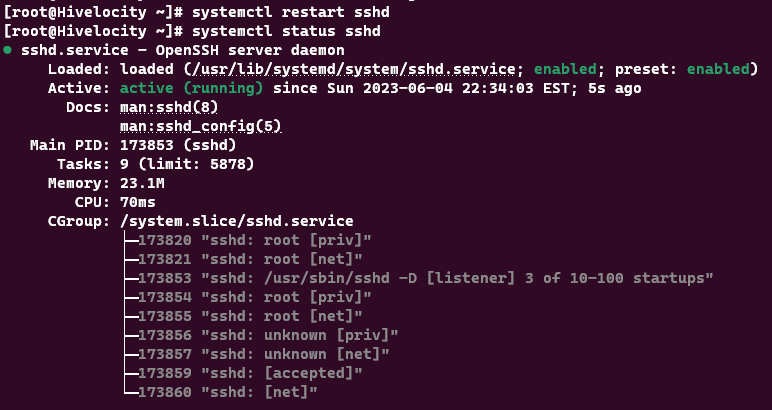
With the above steps finished, this now completes the task and no one can use your root credentials to login to your server remotely via SSH.