Protecting the Production Line: How Enterprise Cloud Safeguards Manufacturing Operations from Cyber Threats
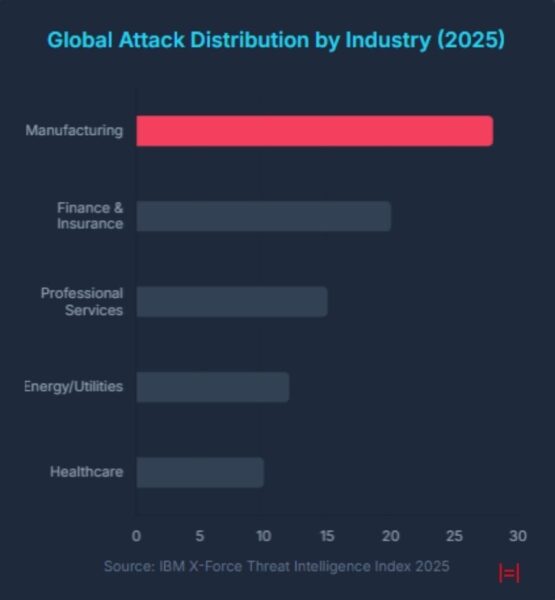
Manufacturing has evolved. The production line is no longer just mechanical; it’s a synchronized digital ecosystem. But this connectivity has introduced a level of vulnerability that was nonexistent in the era of air-gapped systems.
The threat landscape has shifted from opportunistic data theft to targeted operational disruption. According to IBM and Dragos, ransomware attacks on industrial control systems (ICS) doubled in 2022. The financial stakes are staggering:
- $5.56 million: The average total cost of a data breach in the industrial sector (IBM 2024).
- $22,000 per minute: The estimated loss for automotive manufacturers when the production line stops.
For manufacturers operating on Just-in-Time principles, downtime isn’t just an inconvenience—it’s an existential threat.
The Three Threats Stopping Production
- Industrialized Ransomware: Threat actors now target operational capability. By locking Human-Machine Interfaces (HMIs) or Historian databases, they force a complete production stoppage. The cost of downtime often exceeds the ransom itself.
- IP Theft and Espionage: Competitors and nation-state actors target proprietary designs and trade secrets. These breaches erode competitive advantage and are often difficult to detect until the damage is done.
- Supply Chain Cascades: Manufacturers rely on a complex web of suppliers. A breach at a third-party vendor can bypass your perimeter, providing attackers a backdoor into your critical systems.
Why Public Cloud Isn’t Enough
Many manufacturers find that standard multi-tenant public clouds struggle to meet the rigid security and performance requirements of the factory floor. The “noisy neighbor” effect can introduce latency, while shared resources complicate compliance with standards like CMMC 2.0.
To secure the production line, manufacturers are turning to Enterprise Cloud solutions that offer physical isolation and deterministic performance.
The Hivelocity Enterprise Cloud Solution
Hivelocity’s Enterprise Cloud is built for organizations that cannot afford to compromise on security or uptime. We provide a VMware-based environment backed by Pure Storage, designed to act as a digital fortress for your operations.
1. Physical Isolation and Dedicated Hosts
Unlike standard public clouds, Hivelocity offers dedicated hosts. This means your critical data and applications reside on physically isolated hardware, eliminating resource contention and significantly reducing your attack surface. It provides the control of on-premises hardware with the flexibility of the cloud.
2. Managed Security and Patching
Legacy systems and unpatched vulnerabilities are top entry points for attackers. With our managed service tiers, Hivelocity’s engineers handle the heavy lifting of infrastructure security, including proactive updates and patch management. We act as an extension of your IT team, letting you focus on production rather than maintenance.
3. Resilience with Veeam and Zerto
A robust defense requires a recovery plan. Hivelocity integrates world-class data protection directly into your cloud environment:
- Veeam Backup & Replication: Ensures your data is immutable and recoverable, neutralizing the threat of ransomware encryption.
- Zerto DRaaS: Provides near-synchronous replication for disaster recovery, ensuring that if a site goes down, your operations can spin up elsewhere in seconds, not days.

Click for larger view and download
5 Steps to Fortify Your Operations Today
Defense requires more than just the right platform. Implement these strategies to harden your security posture immediately:
- Segment Networks: Strictly separate IT (corporate) and OT (operational) networks to prevent lateral movement by attackers.
- Enforce Least Privilege: Use Role-Based Access Control (RBAC) to ensure employees and vendors only have access to the specific data they need.
- Deploy Immutable Backups: Ensure you have a data copy that cannot be altered or deleted, serving as your fail-safe against ransomware.
- Audit Your Supply Chain: Demand transparency from your software and cloud providers regarding their own security protocols.
- Test Your DR Plan: A disaster recovery plan is only a theory until it’s tested. Run regular drills to validate your Recovery Time Objectives (RTO).
Don’t wait for a breach to expose the gaps in your infrastructure. Hivelocity provides the dedicated, secure foundation modern manufacturers need to keep the line moving.
Explore Hivelocity Enterprise Cloud.
Enhance your enterprise cloud experience with world-class backup and replication with Veeam and DRaaS solutions with Zerto.